📚 Cybersecurity & Cloud Engineering Series⚓︎
Welcome to our multi-book series dedicated to professionals in cybersecurity, cloud architecture, and infrastructure engineering.
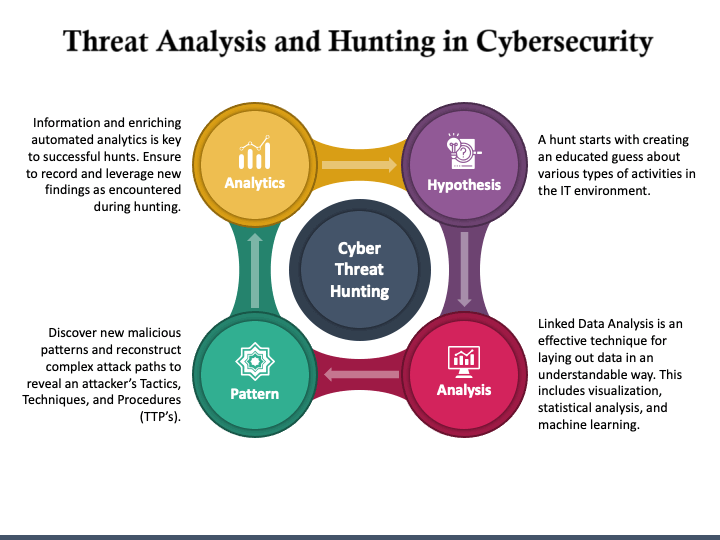
🔍 Threat Analysis & Hunting⚓︎
Threat hunting is a proactive approach in cybersecurity, focused on detecting threats that evade traditional security solutions. This chapter introduces core concepts, methodologies, and the value threat hunting brings to modern organizations.
➡️ Go to Book
🛡️Cybersecurity⚓︎
🔓 Vulnerability Management⚓︎
In cybersecurity, the term "vulnerable" refers to a weakness or flaw in a system, software, hardware, or network that could be exploited by a threat actor (like a hacker or malicious entity) to gain unauthorized access, cause damage, or perform malicious actions.

Types of Vulnerabilities
Buffer Overflow: When more data is written to a buffer than it can hold, causing memory corruption and potential arbitrary code execution.
SQL Injection: An attacker injects malicious SQL queries into input fields to manipulate or steal data from a database.
Cross-Site Scripting (XSS): Malicious scripts are injected into websites, which then execute in a victim’s browser, potentially stealing cookies, session data, or other sensitive information.
Cross-Site Request Forgery (CSRF): Attackers trick a user into making an unwanted request, such as changing account details, by exploiting their authenticated session.
Privilege Escalation: Attackers gain higher privileges (like root or administrator access) by exploiting flaws in the OS or software.
Denial of Service (DoS): Vulnerabilities that allow attackers to overwhelm a system with excessive requests, causing it to become unresponsive.
Race Condition: A situation where multiple processes try to access or modify the same resource simultaneously, leading to unpredictable behavior or unauthorized access.
Zero-Day Vulnerabilities: A flaw that is unknown to the vendor or the public and can be exploited before it’s patched (hence, "zero-day").
Insecure Direct Object References (IDOR): An attacker can access or modify resources they shouldn’t be able to by manipulating the URL or request parameters.
Misconfiguration: Improperly configured security settings, permissions, or firewall rules, such as leaving default passwords or exposing sensitive services to the internet.
➡️ Go to Book
🛠 Contributors & License⚓︎
Maintained by security professionals and open to community contributions.
Licensed under CC BY 4.0.